This article is the first one in a
It all started with Satoshi Nakamoto’s whitepaper that was published in 2008. Before the now-legendary paper was published there was no known way to create an authentic digital currency without the help of a centralized authority.
The main issue here was the problem of double spending.
What is the Double Spending Problem?
Any digital currency is just another form of digital files. There is no authority stopping anyone from copying these files and sending them to multiple people. For instance assume that Peter has a file that has been saved locally to his computer. There is nothing preventing Peter from simply copying this file as many times as he wants and sharing the file with multiple individuals. This is known as the double spending problem. This same principle can be applied to digital currencies, which is portrayed in the image below.
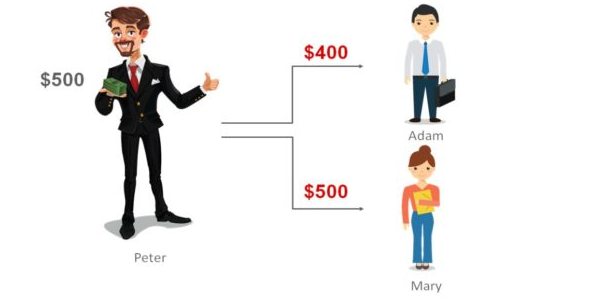
The only solution to this issue, before Bitcoin, was to trust a central authority to manage these digital files. In such a system, if a single authority cheats – then the user is doomed and the only way for them to reinforce the breached contract is by taking help of the law, which we know is slow, expensive and uncertain. Another big issue was that this centralization makes the system prone to a single point of failure.
Satoshi Nakamoto’s whitepaper gave a solution for the double spending problem and made it possible to make digital payments without the need for a central authority, which was Bitcoin. The paper solved this problem by using a trustless peer to peer network. Instead of storing data only in a centralized ledger the data is broadcasted throughout the network using gossip protocol and every peer updates its own ledger. This way within a small period of time, the entire network has the same copy of ledger, or we can say that the whole network has the same state.
What is a transaction and what is a block?
A transaction is an exchange of assets between 2 users, for example, bitcoins are assets on the bitcoin blockchain. An exchange of bitcoins among peers is known as a transaction. A block is the collection of these transactions. Every single transaction is not propagated throughout the network, instead, a block once filled is propagated in the network. Every block has a fixed maximum size or the number of maximum number of transactions it can have.

All the blocks are lined up one after other and each block includes the hash of the previous block, in this way forming a chain.
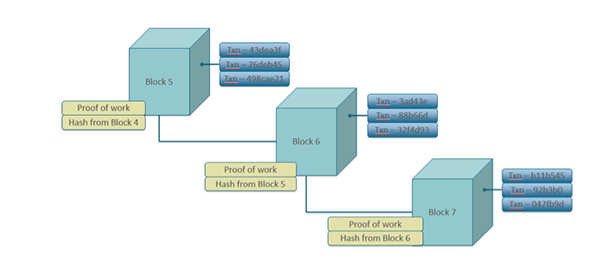
How is double spending prevented?
A network is composed of nodes (the peers). Some of the nodes are miners. Any node can become a miner, and no permission is needed because it is a public ledger. In simplest terms, miners compete with each other to solve a computational puzzle. One who solves it first broadcasts the block which has a collection of transactions – that miner validates and confirms that there is no double spending. He also broadcasts the solution of the puzzle so that everyone can verify that he has actually solved the puzzle. All nodes also verify the transactions in the block before adding that block in their own copy of ledger. In case a miner has added a double spent transaction in the block the nodes will reject that block and that block will be dropped.
Why would anyone want to be a miner?
A miner who solves the puzzle and broadcasts the block gets a fixed number of native currency. For example: bitcoins in bitcoin blockchain, miner also gets the transaction fees paid by the user. Miner can choose the transactions that he wants to add in his block,
Miner
Why do we need to waste all this energy to solve a puzzle?
Consider the following attack scenario to understand.
Suppose an attacker wants to double spend a transaction that is in block number 1000 and current block number is 1005. The attacker will make a change in block number 1000 but he can change it only in his own node, as the state of blockchain is same at all other nodes. Attacker forks his own chain from the main chain and adds new blocks to this forked chain and hopes that everyone in the network accepts his chain.
There can be two cases from here.
- Attacker’s hashing power (computational power to solve the puzzle) is less
then 50% of the total hashing power. The speed with which his chain size increases will be less than that of the honest chain. - Attacker’s hashing power is more
then 50% of the total hashing power. The speed with which his chain size increases will be more than that of the honest chain.
Longest Chain Rule
All nodes follow the longest chain rule i.e. the longest chain has most work done on it and so it is honest.
So in the former case, attacker chain length will be less than honest chain, the probability of successful attack is less and hence attacker will not be able to double spend.
In the latter case attacker chain length will get longer than honest chain and suppose that after 2 hours, length of honest chain is now 1010 and that of attacker chain is 1011. All nodes will update to the chain of attacker and the blocks from 1000 to 1010 mined in honest chain will be dropped. The computational power spent to change a block increases with the depth of the block being changed. If the value of double spending exceeds the computational power cost, it is not sensible to perform such an attack.
Once many blocks are mined on top of a block the transactions in that block may be considered as irreversible.This attack scenario explains the importance of solving a computational expensive puzzle.
This requirement that expensive computations be performed in order to facilitate transactions on the blockchain is popularly known as Proof Of Work.

Scalability Issues with Blockchain

Bitcoin and Ethereum are based on the
The throughput is small, for bitcoin it is in single digits while throughput of Visa is in 1000s of tranactions per second. As more and more people start adopting bitcoin, the transaction fees will rise (demand is more than supply) thus making small value transactions in bitcoin futile (fees will be more than the value of
Recently on Ethereum, a game named cryptokitties took off and the traffic became high thus increasing the transaction fees and number of pending transactions by many folds. The issue of scalability is the biggest barrier for mass adoption of these currencies.
Throughput of blockchain is limited by the fixed size of a block and the propagation time of a new block through the whole peer to peer network.
Solutions to the Scalability Problem
The scalability issue is the most prominent field of research in the blockchain world. Many different solutions are being proposed to solve the issue. These solutions can be classified into two types:
Layer 1 Solutions
These solutions change the blockchain protocols to deal with the problem of scalability.
Segregated Witness (SegWit)
This is exclusive to Bitcoin. It is a small improvement in the bitcoin protocol which increases the throughput by fitting more transactions in a single block by re-weighing the signatures of transaction data. Signature data of every transaction is moved from the main chain to the parallel side chain which frees up space in the block. Still, the throughput will be in single digits and hence not a solution for mass adoption of bitcoin.
Block Size Increase
Right now as per bitcoin protocol the size of the block is limited to 1 MB this limits the throughput of the bitcoin network.
Why don’t we just increase the size of the block?
This is currently a topic of debate, a part of bitcoin community believes that increasing block size is necessary for mass adoption of Bitcoin. As it will prevent increase of gas price at times of high traffic. They also believe that SegWit is not a permanent fix and size of blocks must be increased. When SegWit was implemented this community forked a new blockchain ‘Bitcoin Cash’ which does not implement SegWit and has a block size of 8MB.
Other part of the community believes that increasing the block size will centralize the Bitcoin network. As the block size increases, the amount of processing power required to mine a block will increase. This will make it impossible for small scale miners to mine a block and all the power will shift to a handful of miners. Thus making 51% attack more possible. Some of them also believe that Bitcoin should only be used as a store of value like gold.
Increasing block size will cause other problems as well. Size of the block is related to the propagation time of a new block through the network. More the size of the block more time it takes for each node to validate transactions in it. A node propagates a block only after it has validated the block. Increasing block size will increase the propagation time of new block through the whole network.
Chain Reorganization
Suppose there are 2 honest miners A and B, in two different parts of the world. A solves the puzzle and broadcasts his block in the network. Before this block reaches B, B has also solved the puzzle and he also broadcasts his block. So some of the nodes in the network have added the block mined by A to their local copy of ledger and others have added the block mined by B. Ultimately one of these blocks is dropped. This is known as chain reorganization.
Although the dropped block had honest transactions it got dropped. All the hashrate is wasted which could have been used to mine another block which would have made the network more secure. More the size of the block more the wastage of hashrate.
Sharding
Any transaction that takes place on the ethereum network has to be validated and stored by each node in the network so that every node has the same state. This puts a limit on the throughput on a protocol level. Hence, no matter what the implementation, without changing the protocol it is difficult to solve the scalability issue.
What if all nodes don’t have to process each transaction? The network is divided into some sections which can work semi-independently. Each section could process a different batch of transactions and hence increase the throughput by many folds. Each of these sections is termed as ‘shard’. This is the idea behind sharding.
Layer 2 Solutions
Layer 2 solutions don’t change anything on the protocol level. They are built on top of the same protocols, a kind of a second layer on top of Layer1.
The purpose is to make maximum possible use from available throughput. We try to squeeze in maximum possible number of operations. This works by creating a second layer which is hinged around first layer. All the transactions in Layer2 take place off chain, those transactions need not to be included in Layer1 instantly. All the transactions are recorded off chain. The net result is finally pushed in the Layer1 thus giving them security of Layer 1.
Although the finality of the transaction is less in Layer2 transactions than Layer1 transactions. Layer2 transactions are also secure and final enough for many practical purposes.
State Channels and Plasma are a few examples of the proposed Layer2 solutions. We will discuss them here.
Must read: “Victory Royale: How Blockchain Could Fix Fortnite“